
Why Is Identity Verification Essential in the Telecom Industry?
4 Aug 2020
Telecom industry has a high fraud risk. SIM card fraud is a growing concern among mobile users across the globe. From ordinary citizens to the heads of global phenomena like Twitter, no one is completely safe from having their mobile systems hacked, having their personal information stolen, and their entire life’s saving being wiped clean right from under them. Companies like GetID are dedicated to helping your organization enable security and ID checks to ensure that anyone accessing your system is exactly who they say they are. With ironclad security through digital ID checks, customers can protect their assets and mobile organizations can secure their credibility and service.
The use of mobile devices has increased exponentially over the past few years and it is projected that by next year (2021), the number of these mobile users is going to cross 7 billion! However, with everything going digital, many Telcos have also started exploring the concept of online onboarding of new prepaid SIM users as a means of saving costs, onboarding time and overall making their entire experience more customer-friendly. This online onboarding comes with the risk of dealing with customers who might be using stolen identities, may be persons of interest, and more. Mobile organizations need to work with security companies to ensure secure and accurate identity verification in all online dealing with customers.
Onboarding Prepaid SIM Card Users
GetID is involved in the process of helping telecommunication industry onboard new prepaid SIM card users.
Helping new SIM card users onboard remotely brings with it a new challenge: online ID verification. Online verification is designed to ensure the safety of existing user accounts and prevent problems like fraud, money laundering and other criminal activities. With GetID verification software, telecom companies can take care of all these problems in one place.
GetID software complies with local and global regulations, makes onboarding customers quick and secure and keeps both the company and its customers safe from fraudulent activity by ensuring that anyone trying to communicate with the Telco company is exactly who they say they are.
Read on as we look at the growing concern over online ID verification, how countries across the globe are setting up licensing regulations for protection against security threats, and more.
Types of Fraud
Any activity by a mobile user can expose them and their mobile operating company to the risk of dealing with malicious activity. Mobile devices are being used for communication, monetary transactions, work and more. Through these devices, users can store their private and personal information regarding many aspects of our lives, including our online activity such as social media accounts, emails, and more.

But while our little SIMs help us navigate through our daily lives and always stay connected, if a SIM gets hacked, stolen, or lost, SIM swap attacks become a harsh reality. In fact, it was reported late last year that banking customers lost £9.1 million over a period of 5 years due to SIM swap scams.
Identifying SIM Swap Fraud & Protecting Yourself from It
SIM swapping (also known as SIM Jacking) occurs when a person’s personal contacts are transferred to the SIM of a malicious online user through digital hacking techniques. Not only does this expose the user’s contacts to misuse, but it poses a much bigger threat: these hackers can gain access to any information linked to your SIM card ranging from passwords to email access to even banking details.
How Does SIM Swap Occur?
SIM swap fraud can happen due to any loose ends during verification, such as not enabling 2-factor authentication, etc. Once a scammer has hacked into your system, they are able to get a hold of your basic personal data, including the mobile number your SIM is registered on. They may then contact your mobile operator claiming that their SIM card is lost and will then be able to get a new SIM issued under your name. Once they have this new SIM card, they can review your mobile communication with banks and other organizations that you have personal dealings with.
Once they’re in your system, they can reset new passwords that will essentially lock you out and give them complete access to items such as your bank account. From here on, depending on who has hacked your account, you may be held guilty of terrorist activity, money laundering and other serious crimes.
SIM swap hackers may limit their activities to the small scale of monetary gain through your bank access or on a larger scale where they may target multiple SIM users at the same time to extort large sums of money. Over the years, SIM swap fraud has become more dangerous, with criminals getting millions of dollars out of their victims.
Identifying SIM Swap Fraud
Many times, victims don’t even know that they have been subjected to SIM swap scams until it’s too late. Here are some warning signs to keep an eye out to try and identify if you’ve been hacked and secure your accounts before any real damage has been caused:
- Any activity on your social media accounts such as a post or a comment you didn’t make is a warning sign.
- If your phone calls and text messages are showing errors or not reaching their recipients, there is a possibility that your hacker may have blocked the old SIM in an attempt to have a new one issued.
- Don’t ignore any messages, calls or emails from your mobile service provider – if you get notified about a new SIM issuance, then you definitely know you’re in danger!
- Similar to suspicious social media activity, if other accounts such as email, banking and more are not working or your credentials are being rejected, reach out to the organization in question without any delay.

How to Protect Yourself from Being a Victim of Fraud
- PIN verification
- 2-factor authentication
- Not sharing any major information on social media platforms
- Checking all security measures on any account you’re creating to have the best security setting possible.
How Lack of ID Verification Aids SIM Swap Scams
Victims of SIM swapping have lost all their money and their entire lives have been turned upside down when hackers steal their personal information. The majority of the fault here comes onto mobile service providers who are not following the security measures that will keep their customers 100% safe. Identity verification checks can prevent hackers from impersonating service users, issuing SIMs under their names and more since they will be unable to get past this security checkpoint. These verification checks may be in the form of a license plate number, birthdate, social security number, and so on.
Securing e-SIMs against Fraud
There is a growing number of users and mobile operators switching to the concept of an e-SIM bypassing the need for the little chip that needs to be inserted into your phone. While many mobile operators claim that it provides the same if not a higher level of security as a regular SIM card, the e-SIM does open a new avenue of fraudulent activity.
While there is an extra form of security since hackers can’t steal the actual mobile device and remove the SIM card, an e-SIM user is at risk of having their IMEI number stolen, which can then be used by the hacker to contact their mobile operator and have a SIM card issued.
SIM Swaps Lead to Identity Theft
The major reason hackers have behind stealing a user’s personal information is to conduct identity theft, which affects hundreds of thousands of people every year.
The Consequences of Fraud for Mobile Operators
Mobile fraud is growing on a massive scale across the globe and in 2019, it was responsible for a $28.3 billion loss for the telecommunications industry. The most recent breach in the UK saw the personal information of 11.5 million customers of a mobile operator being leaked. When mobile fraud occurs on such a massive scale, it reduces the customers’ trust in the mobile service provider to ensure their safety. This is why it’s absolutely crucial for mobile operators to work together with an ID Verification company to set up identity security checks, both to protect their data vault from being hacked and any other malicious occurrence happening to their customers.
When customers lose money through online fraud, their trust in all remote services such as remote mobile services, online banking and more is lost permanently. This not only causes mobile operators to lose customers (and thereby revenue) but also affects their reputation and the number of new customers onboarding is likely to take a hit.
While financial service providers like banks may still be able to provide monetary compensation to their customers, mobile operators must undergo a prolonged period of being associated with having poor security measures in place.
Mobile operators need to constantly expand their efforts on research, introducing newer technology and putting their efforts into providing a secure service for their customers. This is where the need for identity verification comes in:
How Can Identity Verification Help To Detect And Prevent Fraud?
Whether we talk about in-person onboarding or digital onboarding, ID verification is making leaps and bounds in preventing fraudulent activities that put mobile operators and their users at grave risks. Let’s see how this works:
KYC Compliance
Know Your Customer (KYC) is the verification process during the onboarding process or it may even happen with customers who work with the service provider already. KYC is also required for banking customers since the identity verification is meant to mitigate fraud risk for both customers and the service provider.
In many regions, KYC is a government-mandated measure as an AML (Anti-Money Laundering) measure and as a measure to prevent mobile operators from being involved in terrorism funding and assisting politically exposed persons (PEP).
KYC regulations, whether or not they are government-mandated, are key for mobile operators. How do you know your customer is who they say they are? ID verification platforms like GetID use biometric facial recognition, obtaining authentic identification documentation and other measures to create a safe digital working environment for both the customer and the mobile network operator.
KYC compliance also includes running a background check on customers as needed to ensure that they are not PEPs, sanction lists involved in any terrorist activities or people conducting identity theft. For mobile operators, this is optional, depending on the level of security they are trying to implement.
ID Verification for e-SIM Users
e-SIM users who onboard digitally can upload a selfie along with the relevant identification documents onto the mobile operator’s system. The system runs a scan to compare whether the selfie matches the photos on the provided documents.
ID Verification for Online Payments
With more and more mobile operators relying on online payment such as credit cards, hackers have another space to commit fraud. By performing verification checks with each online transaction, companies can ensure that the customers are who they claim to be.
ID Verification for Logins
By securing customer accounts with 2-factor verification and biometric facial recognition, companies can secure the accounts of their customers to maintain the trust of their customers and to build a reputation of being a secure service provider.
Stringent Regulations for Telecom Companies Are Being Implemented Around the World
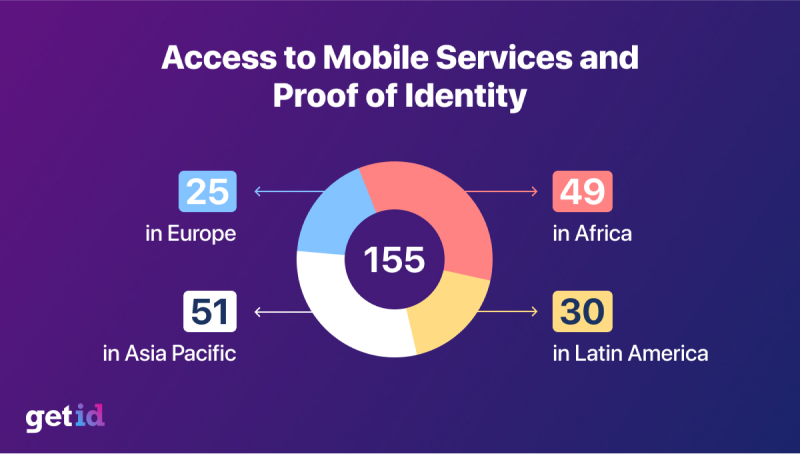
According to the GSMA, since early 2020, the governments in 155 countries require customers to provide proof of identification before registering for and buying a SIM, which also applies to e-SIMs and related products.
Mobile operators need to think about creating a safe and secure environment for those onboarding with them, abide by legal requirements and ensure that their services and sales do not falter due to malicious activity. They also need to consider the implications of identity validation as they switch to remote customer service and onboarding.
No one is truly safe from SIM fraud without ID verification. More recently, Twitter’s CEO, Jack Dorsey, saw his Twitter account being hacked through SIM Card fraud despite the presence of two-factor authentication. It is clear that without identity verification, even these security measures have become outdated.
Regardless of whether the government mandates regulations for identity verification or not, it is an unavoidable measure in order for mobile services to be safe and reliable.
Moreover, mobile services are in constant competition with each other and one security hit is enough to put your reputation in danger to the point where you will lose customers to your competitors.
At the moment, the world has over 5 – 6 billion mobile users and at least 90% of these users are active in countries where ID verification is mandated by the government. However, traditional ID checks are not enough and even now in the United States, for most mobile network operators, SIM card registration is not mandatory opening up leeway for fraudulent activity. The only way around this is with digital and updated verification techniques.
Even in 2020, a number of countries have dealt with growing cases of mobile fraud. Europol alone has dealt with fraud cases costing millions of pounds, some involving dangerous gang members.
Mobile operators intend to tackle these issues with e-SIM usage, but even that requires ID verification to maintain a level of security that cannot be penetrated by hackers.
Precautionary Note for SIM Card Users
Never give away any personal information on phone calls, text messages, or emails. If you suspect or have been the victim of SIM and/or mobile fraud, contact the company whose account information has been stolen from you.
It is advisable to save the customer support helpline of your mobile operator in case you are locked out of your own SIM card and need emergency assistance.
Keep an eye out for suspicious activity and any transactions that were not known to you to ensure that you are not a victim of online fraud.
What Companies like GetID are Responsible for
GetID specializes in identity and document verification and has amassed industry knowledge and security-specific tools to ensure that this verification process is successful and hassle-free.
A combination of documents with AI-based facial recognition is used to verify documentation and perform face matching to provide security clearance to any potential new customers.
GetID works with international providers of AML data covering both local and global sanction lists, AML, anti-terrorism funding PEPs, persons of interest, people on wanted and missing lists with Interpol and the adverse media. You can rely on us to be your go-to KYC provider in accordance with AML compliance.
As a digital service provider, it’s up to you to determine the level of security you need to provide for your customers and select the extent to which all customers must be screened before they are issued a SIM or are given the option to make their online account. The idea is to expand your customer base while simultaneously reducing the number of cases of fraudulent activity, and with GetID, you can make this idea into a reality. Secure your company system today to avoid monetary and reputation losses due to malignant digital activity.
Many Telcos such as T-Mobile have also taken a hit due to the COVID-19 pandemic and with a number of their outlets being shut down, digitally handling customer interactions is becoming the norm. With digital transactions becoming widespread, the need for secure ID verification is greater than ever.
Head on to GetID to get speedy ID checks and to enable regulatory, certified compliance checks to ensure that all your customers onboard safely without having any of their personal data compromised and protect your own company and integrity.