Customer ID verification in 2023 is obligatory for nearly every online business, whether work goes directly with customer’s money or company strives for high scaling. Identity verification is an ultimate beneficial solution for both businesses and customers. Knowing your customer is required by regulations worldwide. Moreover, it makes modern online business safe and creates more trust between companies and their customers.
Introduction
Poor data collection, use, and storage mechanisms within financial institutions worldwide have led to data breaches and hacks, along with financial crime and fraud. Data generation is rocketing due to increased internet usage. In response, institutions struggle to manage the burgeoning volumes of sensitive data on their doorsteps. Vulnerable central data repositories and low-grade security protocols have become a hackers’ circus.
In an attempt to curb the onslaught of data crimes worldwide, increased regulatory compliance is being thrown down. Tighter regulations force companies to install long-winded, expensive data protection processes. While the media swoops down on data breaches and hacks, companies crack down on data usage and storage protocols. Leveraging new technologies, institutions are fast finding ways to increase security and reduce costs, while remaining compliant.
However, the focus on usage and storage often overshadows the importance of the first steps in the data protection chain: accurate, valid identity verification. Strong identity verification mechanisms provide frontline protection for institutions from potentially harmful clients. Robust and reliable ID verification procedures safeguard against identity fraud, hacks, and data breaches for both the customer and the institution.
Unfortunately, a lack of attention to data collection and ID verification has led to the persistence of outdated, manual procedures in organizations. To meet regulatory compliance, these processes are lengthy and expensive. Human-error and questionable security measures pepper these procedures, often resulting in unwitting non-compliance.
Obviously, there is an immediate demand for secure digital identity solutions. Easing friction in the onboarding process, GetID’s multilayered automated digital ID solution is the future of identity verification. The inherent security architecture ensures full regulatory compliance while protecting against data crime. Faster, cheaper, and far more secure than conventional ID verification, GetID offers a user-friendly solution for accurate and efficient Know Your Customer (KYC), Anti-Money Laundering (AML), and Customer Due Diligence (CDD) procedures.
A Quick Background on ID Verification
Data generation is most certainly on the rise. Not only is society increasing their overall internet usage, but more people are also hopping online every day. At the beginning of 2020, the number of bytes in the digital universe was 40 times bigger than the number of stars in the observable universe.
Concurrently, internet use is changing as ‘smart’ technology infiltrates everyday living. From online banking to social media, from ordering takeout to measuring energy usage, data is coming from all angles. The statistics show that in 2021, users sent 197,6 million emails, 69 million messages in WhatsApp and Facebook Messenger, and 2 million Tinder swipes every minute.

As data generation piles up, hard questions arise concerning the correct methods for collecting, using, and storing people’s sensitive personal data. In fact, philosophical musings question what is classified as ‘sensitive’ or ‘personal’ data, and the ownership around these figures.
The effects of not considering these factors can be seen in the soaring numbers of hacks and data breaches at prominent firms. The results of poor data management have led to record highs of identity theft, fraud, and data leaks. Even scarier, data mismanagement has seen inappropriate data sales and sharing, as was the case of the Labour Party in the UK and Facebook.
Fervent consumer concern for these problems has triggered regulatory crackdowns. Mismanagement of sensitive data is being harshly penalized by regulatory bodies worldwide. Recent staunch regulatory standards on data management include CDD updates to the Bank Secrecy Act of 1960 and the 2001 Patriot Act in the USA, and the EU’s General Data Protection Regulation (GDPR). Non-compliance with these protocols results in unbelievable fines.
Take the example of British Airways who were recently fined $235 million. After a hacker attacked data repositories, it was determined that the company’s protocols were not tight enough to prevent the catastrophic data breach. Facebook has also been on the receiving end of such penalties, with a $5 billion fine for inappropriate data sharing.
While attention seems to be on data usage and storage, identity verification is of particular focus in new legislation. Stricter KYC and AML procedures have been imposed on institutions to ensure new clients are who they say they are and are of no threat to the institution. KYC protocols seek to verify a person’s identity by comparing Personal Identifiable Information (PII) to official documents and databases. AML procedures check that the new client has no official sanctions against them, and isn’t a threatening person (Politically Exposed Person or a person of interest). The term ‘Customer Due Diligence’ is the umbrella term for KYC and AML, while also referring to the ongoing maintenance and verification of this data.
The issue is that conventional procedures simply aren’t designed to handle the intense flow of data generation seen today. Traditional manual identity verification procedures are inherently littered with flaws, amplified by the influx of data.

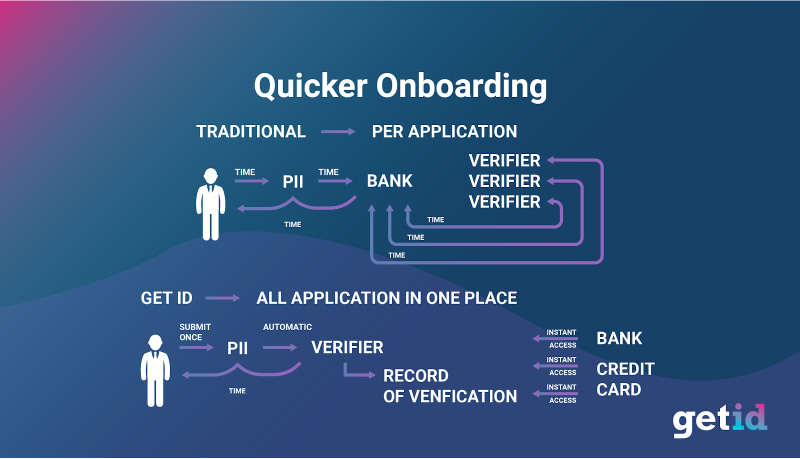
For example, imagine taking out a bank loan. The applicant submits a ream of official documents and personal data to the bank. The bank sends this information to multiple third-party verifiers. These verifiers use official sources to verify the documents are correct and the customer is whom they say they are.
The process itself is arduous as it has to be verified by multiple outside parties. This involves sending information and waiting for a long time. Longer onboarding has led to many customers walking away from applications and services.
Equally, this system is expensive. As more and more data floods institutions, companies need to spend more on hiring increasingly-scarce compliance staff, training existing staff, paying more verifiers, and so on.
On top of that, manual processing has striking security flaws. Firstly, human error in the system leads to problematic inaccuracies. This is especially true of recent times, where image manipulation is far more simple. Nowadays, forged passports and driver’s licenses are easy and cheap to buy online, many of which easily fool expert verifiers. This has sent application fraud through the roof.
Additionally, customer data is shared with multiple outside companies during the manual KYC process. This leaves customers’ PII vulnerable to leaks and hacks out of the original institution’s control. Moreover, data stored within institutions is usually held in central repositories; a single-point-of-failure. This means hackers only need to enter one place to access all customer data.
With such loose identity verification procedures in place, it’s no wonder regulatory bodies are trying to crack the whip. Global financial institutions have already been fined over $26 billion over the last decade for poor ID verification procedures. The FCA, alone, has collected over $500 million in fines in 2019. It seems that non-compliance penalties are only going to get stricter. In line with this, compliance costs will rise.
To solve the bottlenecks for fully-compliant onboarding procedures, manual KYC and AML processing needs to be put out to pasture. It’s time to harness technological advancements to ease the costs, friction, and security flaws intrinsic in manual KYC processing. While mastering this, new ID verification procedures should meet all regulatory compliance — Right now and into the future.
In order to protect customers and businesses against fraud, ID verification processes need to be proactive and accurate. To be affordable and viable, ID verification needs to be convenient. To achieve both of these goals, meet increasing regulatory compliance, and protect against hacks, ID verification needs to be secure.
GetID is pioneering future ID verification procedures to ensure frictionless, fully-compliant client onboarding. Faster, sleeker, and much cheaper, GetID’s automated digital ID verification platform houses revolutionary, decentralized security architecture and state-of-the-art cryptography for robust protection against hackers and fraudsters. Leveraging next-generation technology, GetID’s user-friendly omni-channel platform offers a secure and affordable tool to conveniently comply with stringent data protection regulations.
Why is Effective ID Verification So Crucial?
ID verification procedures are the frontline to safeguarding customers and institutions from potentially harmful fraudsters. Solid KYC, AML, and CCD procedures weed out any prospective threats looking to infiltrate the system for illegitimate means. Without effective identity verification measures, companies are vulnerable to fraud, identity theft, hacks, leaks, breaches, and outrageous non-compliance fines.
By nailing down robust ID verification procedures, institutions can protect themselves and their customers, while complying with regulatory standards. Here’s how effective ID verification processes aid institutions:
Effective ID Verification Eliminates Fraud
In 2018, alone, 14.4 million US citizens were victims of identity fraud. Of that figure, nearly half of this fraud was attributed to new credit card accounts where fraudulent PII documents were used. Over in the UK, application fraud was up 159% last year.

As ID verification procedures are in place to flag these exact issues, it’s clear that widespread ID verification mechanisms need to change. Despite increased compliance, ID verification processes are still hugely vulnerable to fraud. This is both costly and time-consuming for clients and institutions.
Effective ID verification procedures eliminate fraud by removing inaccuracies from the equation. Where currently humans analyze ID documents, it’s clear that there is significant human-error in identifying fraudulent applications. This allows fraudsters to slip through the cracks, entering the system.
GetID’s robust identification verification procedures negate the risk of fraud. This is done using a multi-tiered state-of-the-art identity verification technology stack. GetID’s ID verification stack provides Optical Character Recognition, Face Match verification, and Liveness testing with unprecedented accuracy far beyond human capacity. In this sense, fraudulent applicants can’t slip through.
Effective ID Verification Speeds Up Onboarding
To comply with increasing data regulation, it’s integral that KYC and AML protocols are strictly followed during customer onboarding. Unfortunately, these arduous procedures slow down the onboarding process considerably. This seriously hampers the user experience.
Studies show that customer onboarding time increased by 22% in 2016, and a further 18% in 2017. Banks can now take between 24 and 32 days to process applications. Not only is this a costly wait for institutions, but figures also show that 12% of business account holders change banks due to KYC friction.
The problem with tightening regulation is that KYC and AML procedures become more complex. Institutions need higher numbers of compliance staff and intermediary verifiers to stay compliant. With the flood of data generation increasing the demand for ID verification, there simply isn’t the staff. As data generation shows no sign of dropping, this pattern will continue if more effective ID verification procedures aren’t deployed to increase convenience, speed up processing, and reduce friction.
Manual KYC processing is not the answer here. To stay compliant and keep customers happy, there’s no time to play pass the parcel with multiple third-party verifiers. Instead, GetID has devised an automated ID verification solution. Cutting out the need to send reams of data to third parties, GetID’s solution also removes the need for armies of compliance staff.
Via GetID’s system, customers create a digital ID, submitting their PII only once. Once verified, institutions can access a record of this verification instantly. Institutions no longer need to pester the customers for personal data. For customers and institutions, the whole process if far more user-friendly and takes a fraction of the time.
Effective ID Verification Reduces Costs of Increasing Compliance
Data compliance is costly, especially since regulations are increasing demands on how companies should carry out KYC and AML procedures.
Studies show a 19% increase in KYC customer onboarding costs between 2017 and 2018, with a further jump of 16% in 2018. For the world’s biggest financial institutions, it’s common practice to spend over $100 million annually on KYC compliance. In fact, as far back as 2015, Citibank was spending $1.7 billion a year on data compliance — The figure would likely hover around $3 billion nowadays.
According to the LexisNexis Risk Solutions 2020 True Cost of Financial Crime Compliance Study, global compliance costs increased $33 billion from 2019 to 2020, totaling $213.9 billion. The true cost of compliance during the pandemic has been obscured by the fact that regulators are short-staffed, and they may have been less aggressive with enforcement activities due to the complications that accompany remote workforces, the report notes. Right now, manual KYC procedures cannot scale to provide high-quality ID verification at an affordable cost. This illustrates its inefficacy as a solution.
This is because conventional ID verification procedures are extremely labor-intensive. Huge compliance teams and multitudes of third-party verifiers are needed to cover the sheer volume of data generated. Not only is this costly in itself, but the rising demand for these professionals, lack of qualified candidates, and increasing regulatory pressure all also drive up salary prices and external verification costs.
[postbanner]
How Does GetID Solve This Problem?
GetID provides a state-of-the-art ID verification technology stack with multi-tiered security against fraudulent applications and hackers. Harnessing decentralization and industrial-grade cryptography, GetID offers up a highly-secure ID verification solution that’s fully compliant with current and future regulations. Thanks to the system’s automation, institutions and customers can now benefit from robust, frictionless KYC procedures for a fraction of the cost.
The GetID technology stack includes highly-effective identity verification tools, created for the future if ID verification and KYC.

Optical Character Recognition (OCR) ID Verification
Optical Character Recognition (OCR) is a verification tool that automatically extracts written information from official documents. Whether in digital or paper format, GetID’s OCR technology helps to speed up KYC processes by automating the extraction of information. This data is then verified against official sources. By digitizing this process, GetID removes the tendency for error in manual processing. Equally, speedy computer processing and enhanced accuracy relieve vulnerability to falsified documentation.
For customers, this process means they no longer have to send off precious and sensitive official documents. Instead, OCR scans the documents and automatically extracts the relevant information for verification.
For institutions, automating and digitizing this process removes the data entry inaccuracies. It also speeds up the ID verification process.
Face Match Verification
Face Match technology is biometric facial recognition for identity verification. Far more accurate than a human, Face Match technology identifies human faces. It does this by comparing the applicant’s image to other images in official databases. By matching an applicant’s face to a previous official photograph, the technology verifies an applicant’s identity.
The global facial recognition market expected to reach nearly $9 billion by 2023. That said, it’s clear that human image verification systems are outdated. Removing the room for error, facial recognition technology is far superior at spotting fake photographs than manual, human processing.
This is why GetID employs Face Match verification to complement OCR. Functioning as a second line of defense against fraudulent applications, Face Match guards against fraud and speeds up KYC procedures.
AML/Sanctions Checks
Cutting back onboarding time and slashing costs, GetID relieves the friction associated with AML procedures and sanctions checks by automating the process. In place to flag up potentially harmful people, AML and sanctions checks help to identify money trafficking, financial crimes, terrorist funding, and politically exposed people.
Manual AML procedures require long wait times as the process can be in-depth. Verifiers investigate applicants by running verified documents against the sanctions list. Flagged persons or organizations may be the subject of asset freezing, trade embargoes, diplomatic restrictions, or financial limitations.
Like the above steps in the process, this is done by multiple third-party verifiers. Not only does it take a long time to collect responses from all verifiers, but this part of the process is also error-prone.
By automating this process, verified ID is run against the sanctions list in no time at all. Impeccable digital accuracy means that sanctions will no longer be accidentally missed in processing.
Liveness Check Verification
Liveness checks are a crucial step in effective ID verification. Previously institutions felt safe verifying identity using photographs and official documents. However, a recent spate of face-spoofing proves that neither manual processing nor isolated biometric facial recognition technologies are the solutions.
Just like the use of forged official documents, face-spoofing is used to fool verifiers. In these scams, fraudsters use photos of other people. Social media provides a treasure trove of facial images to use. Fraudsters use these images to ‘spoof’ human verification procedures and low-quality biometric facial recognition software.
Liveness checks solve this problem by having the applicants verify themselves live on camera. Applicants verify their validity by first showing their face, often next to the official ID, like a passport. Next applicants are asked to complete previously undetermined actions, such as blinking, turning their head, or holding a handwritten note. In doing this, they prove the video is live and hasn’t been falsified in preparation.
In this sense, liveness checks speed up verification as they can happen in the moment and within seconds. Where real estate agents now spend up to 4 days a month verifying people’s identity, liveness checks lead to verification in minutes.
Dedicated to speeding up KYC procedures without compromising security, GetID’s Liveness Checks help to validate candidates extremely quickly and accurately. Serving as a safety net, liveness checks also negate any vulnerabilities associated with the isolated use of biometric facial recognition.
By providing a multi-layered identity verification stack, GetID offers a one-stop-shop for identity verification that doesn’t scrimp on security. Instead, GetID uses the multi-tiered to ramp up accuracy and security to ensure full compliance with all data regulations, now and in the future.
Conclusion
ID verification is an integral part of preventing fraud, protecting against hacks and data theft, and safeguarding against money laundering and financial crime. Ineffective identity verification procedures leave institutions vulnerable to these breaches. Not only that, KYC and AML mechanisms put these organizations at risk of non-compliance.
With data compliance regulations ballooning, strong data management and client onboarding procedures are the only defense against unreal non-compliance fines.
However, despite the race to meet compliance, most institutions are still employing manual KYC and AML procedures. Subject to outrageous costs, long processing times, and frequent inaccuracies, manual ID processing is a security nightmare that’s both inconvenient and expensive.


